In late August 2025, Cleafy's Threat Intelligence team discovered Klopatra, a new, highly sophisticated Android malware currently used in active campaigns against financial institutions and their customers. The analysis identified two major botnets targeting users primarily in Spain and Italy, with the number of compromised devices already exceeding 3,000. Klopatra operates as a powerful banking trojan and Remote Access Trojan (RAT), allowing its operators to gain complete control over infected devices, steal sensitive credentials, and execute fraudulent transactions.
What elevates Klopatra above the typical mobile threat is its advanced architecture, built for stealth and resilience. The malware authors have integrated Virbox, a commercial-grade code protection tool rarely seen in the Android threat landscape. This, combined with a strategic shift of core functionalities from Java to native libraries, creates a formidable defensive layer. This design choice drastically reduces its visibility to traditional analysis frameworks and security solutions, applying extensive code obfuscation, anti-debugging mechanisms, and runtime integrity checks to hinder analysis.
This technical sophistication provides a clear footprint of the Threat Actor (TAs). Linguistic clues within the malware's code and intelligence gathered from the Command and Control (C2) infrastructure point decisively to a Turkish-speaking origin. This assessment is corroborated by operational notes left by the attackers themselves, revealing a cohesive and disciplined group managing the entire attack lifecycle, from development to monetization. Klopatra marks a significant step in the professionalization of mobile malware, demonstrating a clear trend of TAs adopting commercial-grade protections to maximize the lifespan and profitability of their operations.
The mobile threat landscape is constantly evolving, with Android banking trojans becoming increasingly bold and technically advanced. However, most of these threats tend to follow recognizable patterns, reusing known code or techniques. Occasionally, a threat emerges that deviates from the norm, signaling a shift in adversary tactics and capabilities.
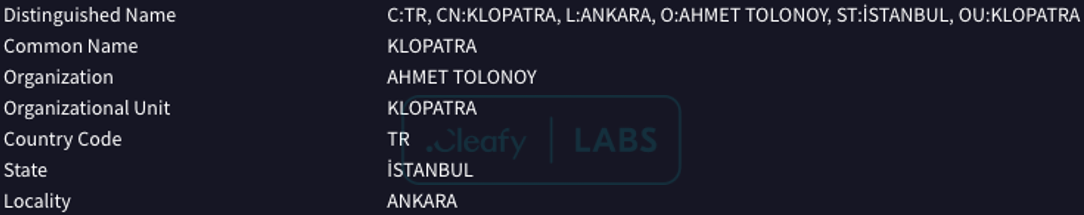
Klopatra is one such threat. Initially discovered by Cleafy's automated detection systems due to behavioral anomalies indicative of sophisticated activity, it quickly stood out as a previously undocumented malware. The analysis revealed no connections to existing malware families, prompting the team to classify it as a new family. The name "Klopatra" was derived from the name of a certificate embedded in one of the first analyzed samples (March 2025), an artifact left by the developers that provided the first clue to its identity.
This report provides a comprehensive technical analysis of Klopatra. It explores its unique, evasion-focused architecture, its powerful capabilities as a financial fraud tool, the operational infrastructure supporting active campaigns, and the evidence that conclusively links the operation to a Turkish-speaking group. Through this analysis, Klopatra emerges as an immediate threat to financial institutions and a harbinger of a new wave of mobile malware adopting professional-grade obfuscation techniques to evade defenses, which has already been seen on other modern Android banking trojans.
Klopatra's effectiveness lies in a carefully orchestrated infection chain, which begins with social engineering and culminates in the complete takeover of the victim's device. Each stage is designed to overcome the defenses of the user and the Android operating system.
The initial phase of the attack relies on a dropper application, a lure designed to appear legitimate and desirable. In this case, the dropper masquerades as an IPTV application called "Mobdro Pro IP TV + VPN," promising access to high-quality television channels. This choice is not accidental; pirated streaming applications are very popular, and users are often willing to install them from unofficial sources, bypassing the protections of the Google Play Store.
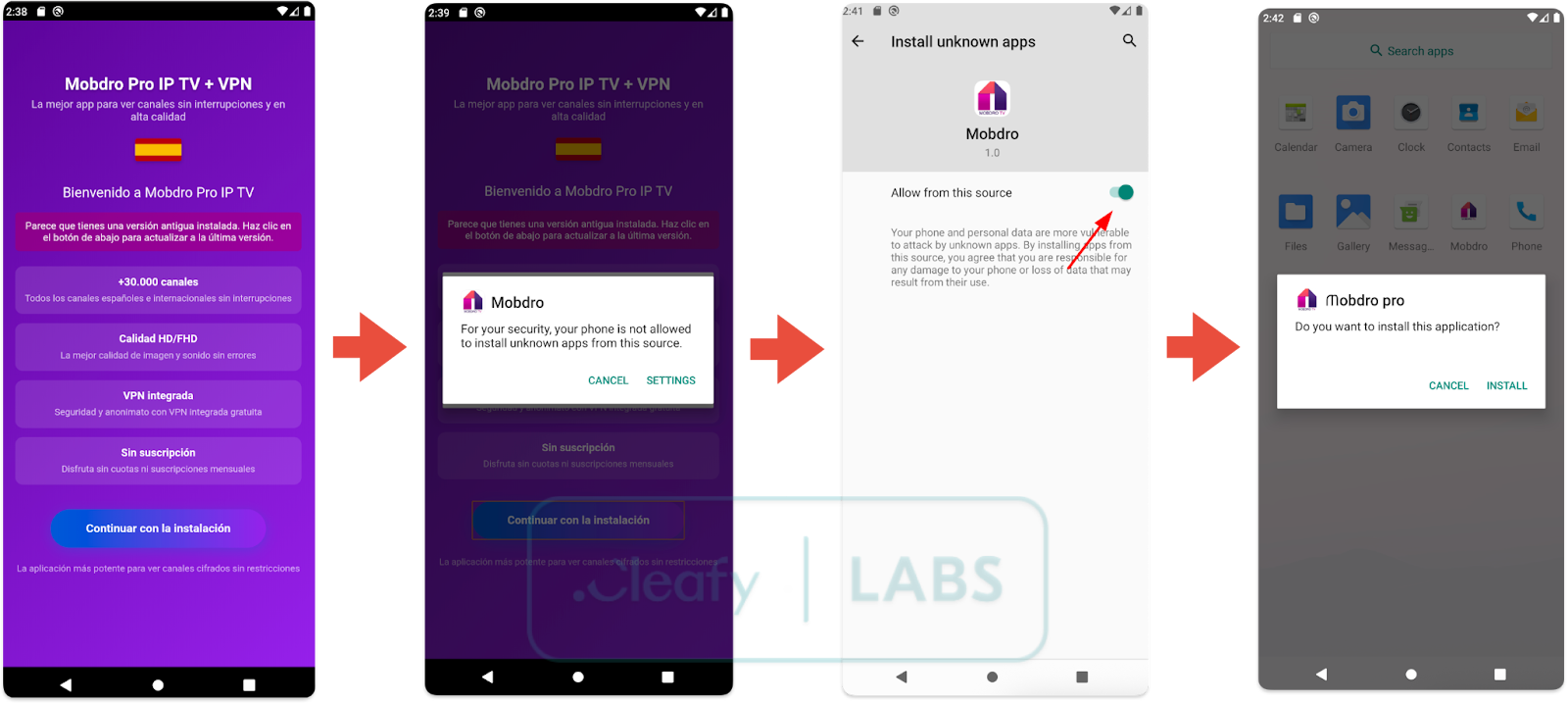
Once installed, the dropper application has a single purpose: to convince the user to grant critical permission, which is the ability to install packages from unknown sources (REQUEST_INSTALL_PACKAGES). To achieve this, the app presents a simple user interface with a button inviting users to "continue with the installation." Tapping this button redirects the user to Android's system settings and instructs them to grant the permission.
Technically, the dropper uses a technique known as "JSON Packer" to hide the real malicious payload within its resources. This serves as a first layer of evasion, making it more difficult for static analysis tools to identify the malicious nature of the initial application immediately. Once permission is obtained, the dropper silently extracts and installs the main Klopatra payload, completing the initial installation process.
Once the main Klopatra payload is installed, the real threat manifests. The malware immediately requests a wide range of permissions, but one is crucial for its success: the Android Accessibility Services permission.
Accessibility Services are a powerful framework designed to assist users with disabilities. They allow applications to read screen content and perform actions on behalf of the user. In the hands of malware, this functionality becomes a weapon.
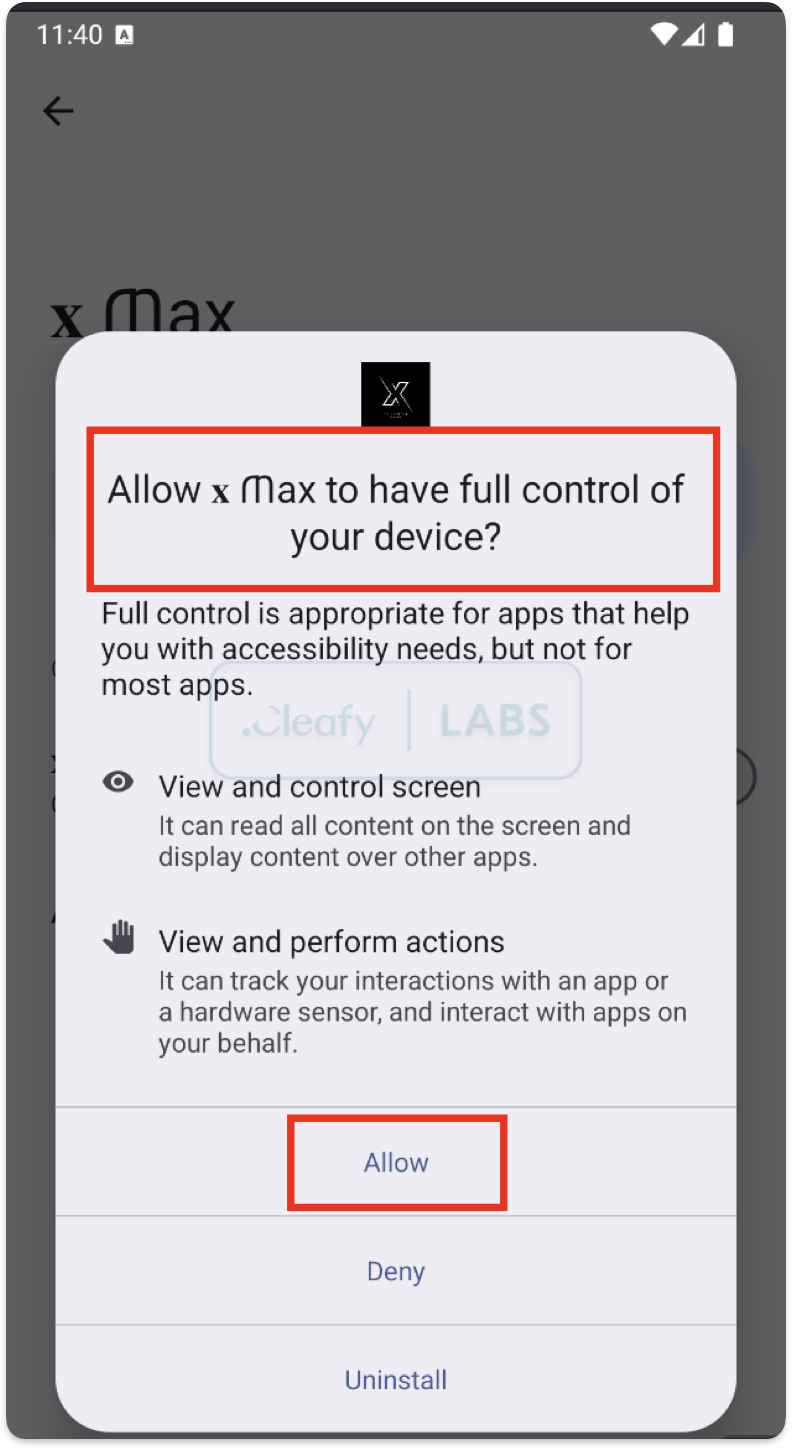
This single permission grants the malware almost unlimited powers over the device :
The abuse of Accessibility Services is the cornerstone of modern banking malware fraud. The technical mechanism turns a malware infection into a direct financial loss, allowing Klopatra to operate with the same level of authority as the legitimate user, but completely invisibly.
Klopatra's internal code structure reveals a level of sophistication that sets it apart from most Android malware. Its developers have made deliberate design choices to maximize evasion, resilience, and operational effectiveness.
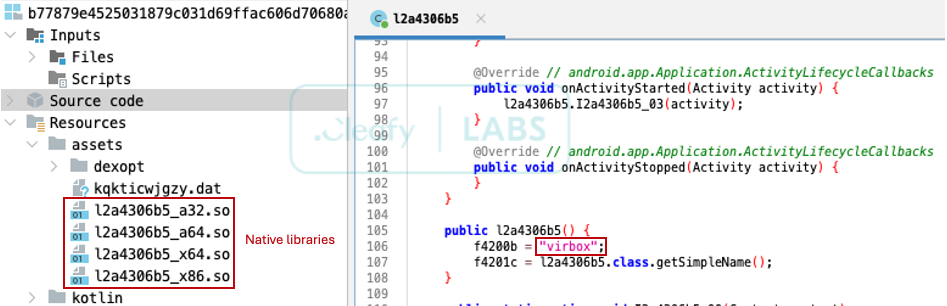
The most innovative feature of Klopatra is its multi-layered approach to evading analysis. At the heart of this strategy is the integration of Virbox, a Chinese commercial software protection solution. While using commercial packers and protectors like VMProtect is standard practice in Windows malware, its adoption in the mobile landscape, particularly on Android, is still rare. This choice signals a significant escalation, indicating that operators invest financial resources to protect their malicious "assets."
Adopting Virbox is not a purely technical decision, but a strategic one. It drastically increases the time and expertise required for security researchers to reverse-engineer the malware. Virbox is combined with a firm reliance on native libraries (C/C++ code). Unlike typical Android malware that implements most of its logic in Java/Kotlin, Klopatra shifts its core functionalities to the native layer. This strategy offers two main advantages:
At its core, Klopatra is a powerful Remote Access Trojan (RAT). It provides operators with granular, real-time control over the infected device. This capability is implemented through two main VNC (Virtual Network Computing) features:
The level of control is highly detailed, as demonstrated by the list of C2 commands (see Appendix A). Operators can perform a wide range of actions, including simulating taps at specific coordinates (click_coord), system button presses like "back" (global_action_back) and "home" (global_action_home), and even executing complex gestures like swipes (swipe_up, swipe_down) and long-presses.
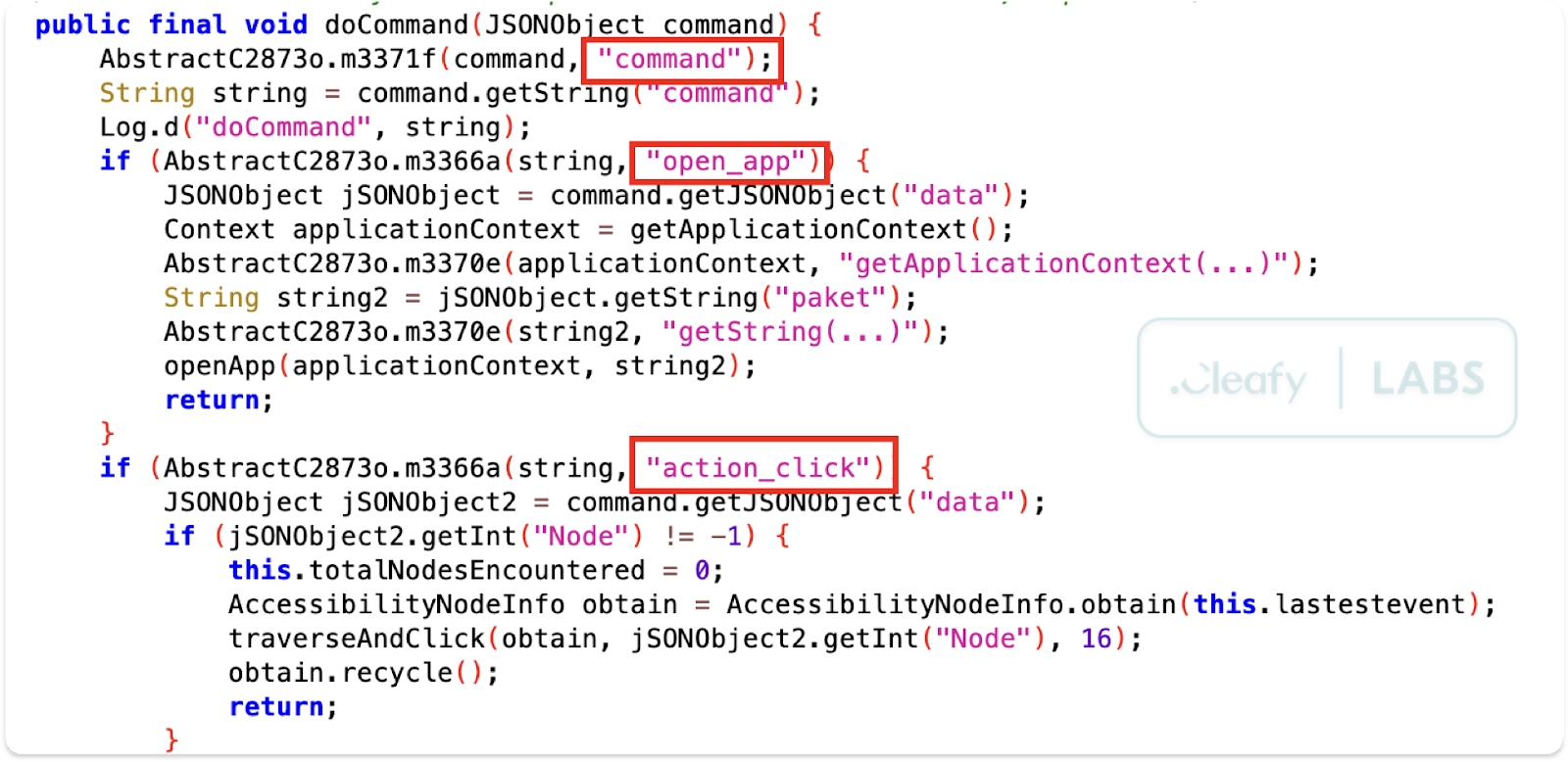
In addition to direct device control, Klopatra employs the classic technique of overlay attacks for large-scale credential theft. The malware maintains a list of target financial and cryptocurrency applications. When it detects the user opening one of these applications, Klopatra sends a request to the C2 server.
The server responds with custom HTML content, which the malware displays as a dialog box over the legitimate app (via the open_enj command). This dialog box perfectly mimics the banking app's login screen, tricking users into entering their username and password. These credentials are captured and immediately sent to the C2 server.
In parallel, Klopatra performs comprehensive data collection. It gathers device information (model, manufacturer, battery level), a list of all installed applications (paketleri_al), and captures sensitive data such as keystrokes and clipboard content. All collected data is structured into a JSON object, Base64-encoded, and sent to the C2, providing operators with a detailed profile of each victim.
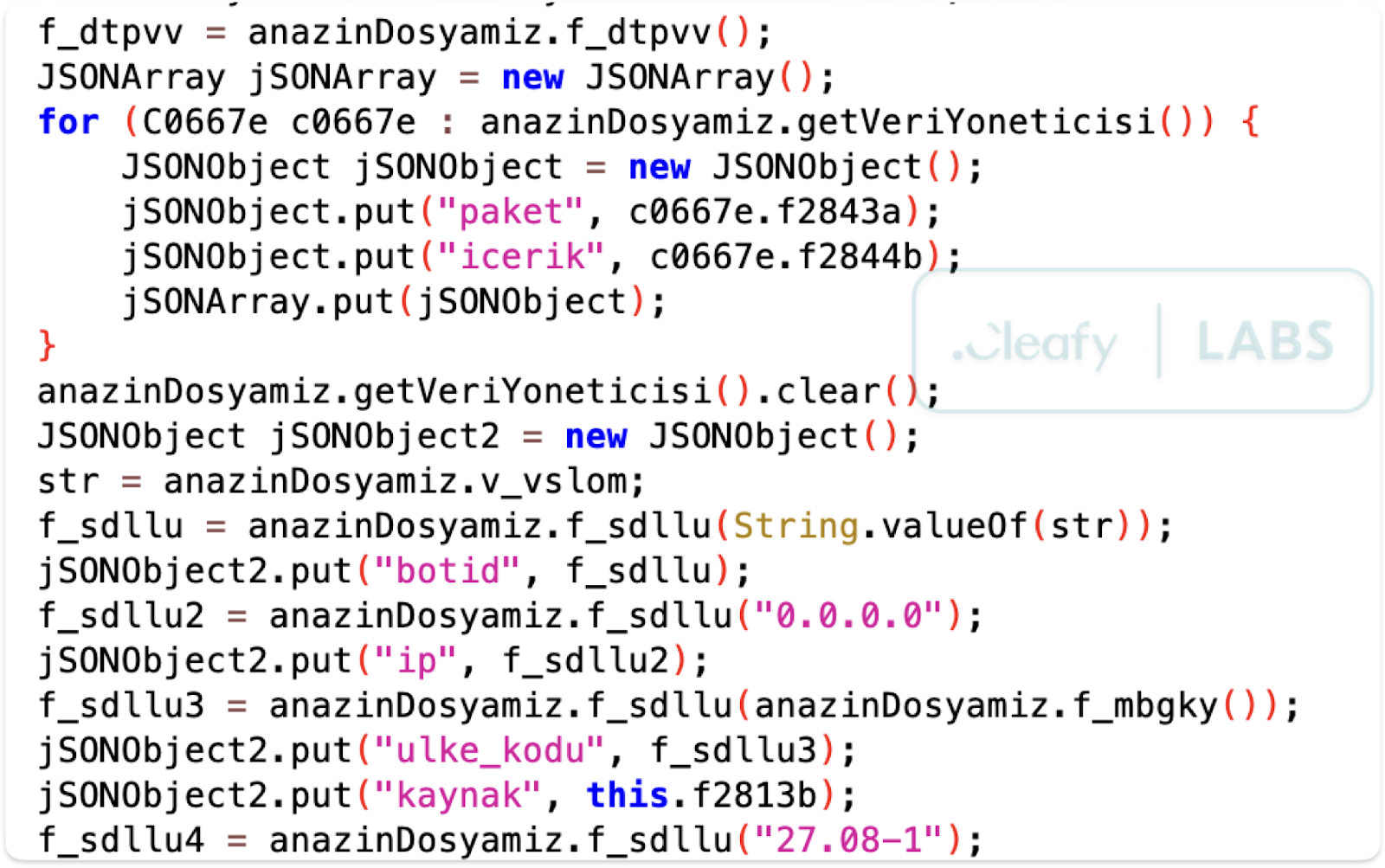
Klopatra is designed to survive on the device for as long as possible. It uses Accessibility Services privileges to self-grant additional permissions, programmatically clicking "Allow" or "OK" buttons in system dialogs. It autonomously navigates to the battery optimization settings (command pil_opt) to add itself to the exception list, preventing the operating system from terminating its background processes.
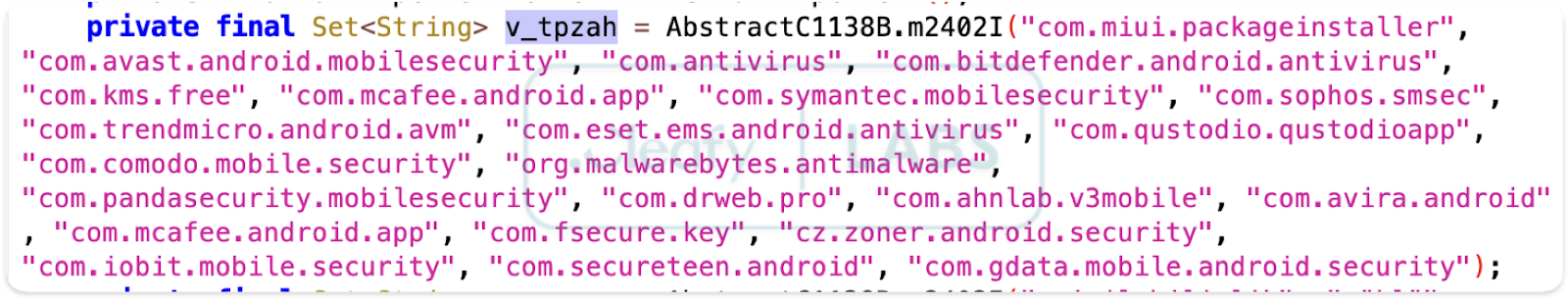
Furthermore, Klopatra adopts active defensive measures. It contains a hardcoded list of package names belonging to popular security and AV solutions. If it detects one of these apps installed on the device, it may attempt to uninstall it to eliminate threats to its operation. Finally, it can simulate the "back" button press to prevent the user from easily accessing the settings screens where they might attempt to uninstall the malware.
Malware analysis goes beyond its code; investigating who is behind it is crucial to understanding the threat. In the case of Klopatra, multiple lines of evidence converge, painting a clear picture of a Turkish-speaking criminal group.
The first clues emerged directly from the malware's code. Function and variable names, left by the developers, were in Turkish. For example, a central function for handling remote commands was named ArkaUcKomutIsleyicisi, which roughly translates to "Backend Command Handler."
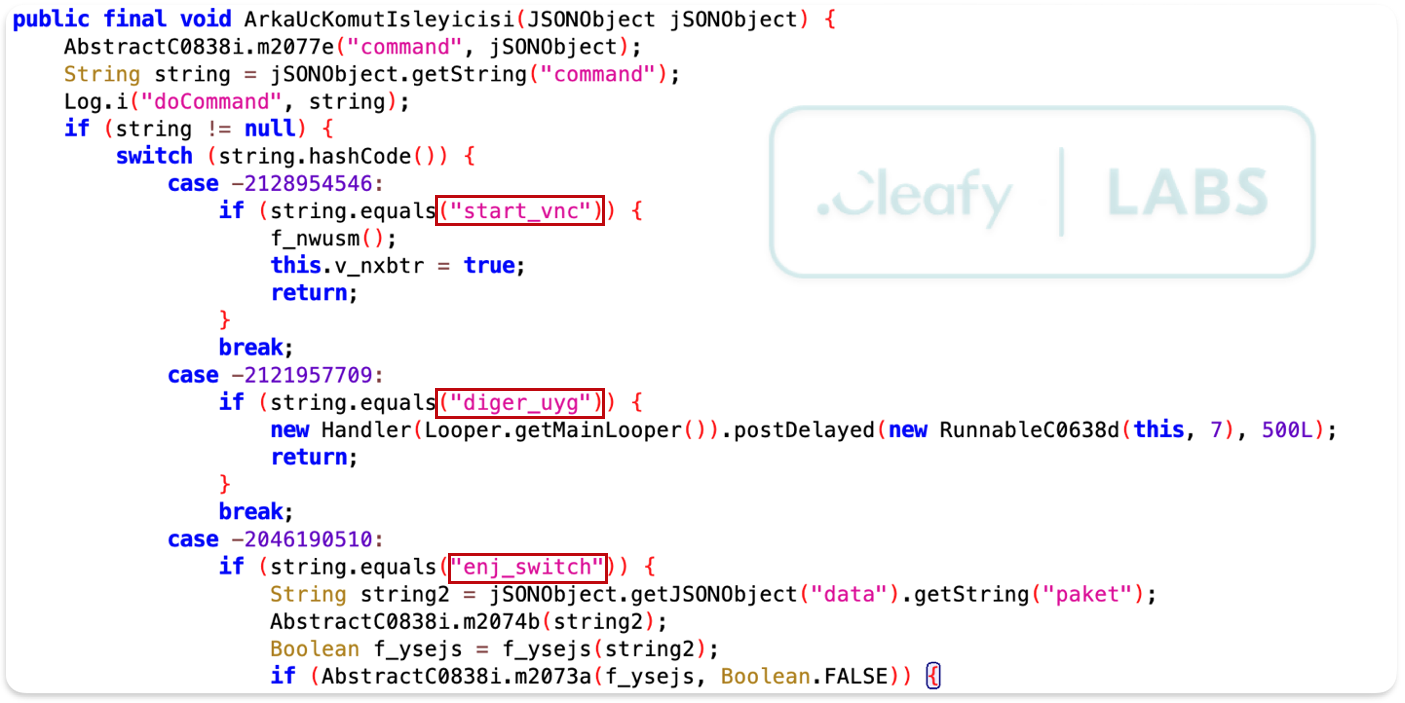
This linguistic footprint extended to the Command and Control infrastructure. Analysis of the JSON responses sent by the C2 servers revealed that many field names were Turkish words. This is a strong indicator, as the control panel's structure reflects the developers' native language. Key fields included :
These fields confirm the Turkish origin and offer insight into the operators' TTPs (Tactics, Techniques, and Procedures), showing how they manage and prioritize compromised devices.
The bot_notu field proved to be a goldmine for intelligence, providing a direct window into human interactions with the control panel. Analysis of a data dump from one of the C2 servers uncovered a particularly revealing note associated with a specific bot: "7k atılan piç şifre z".
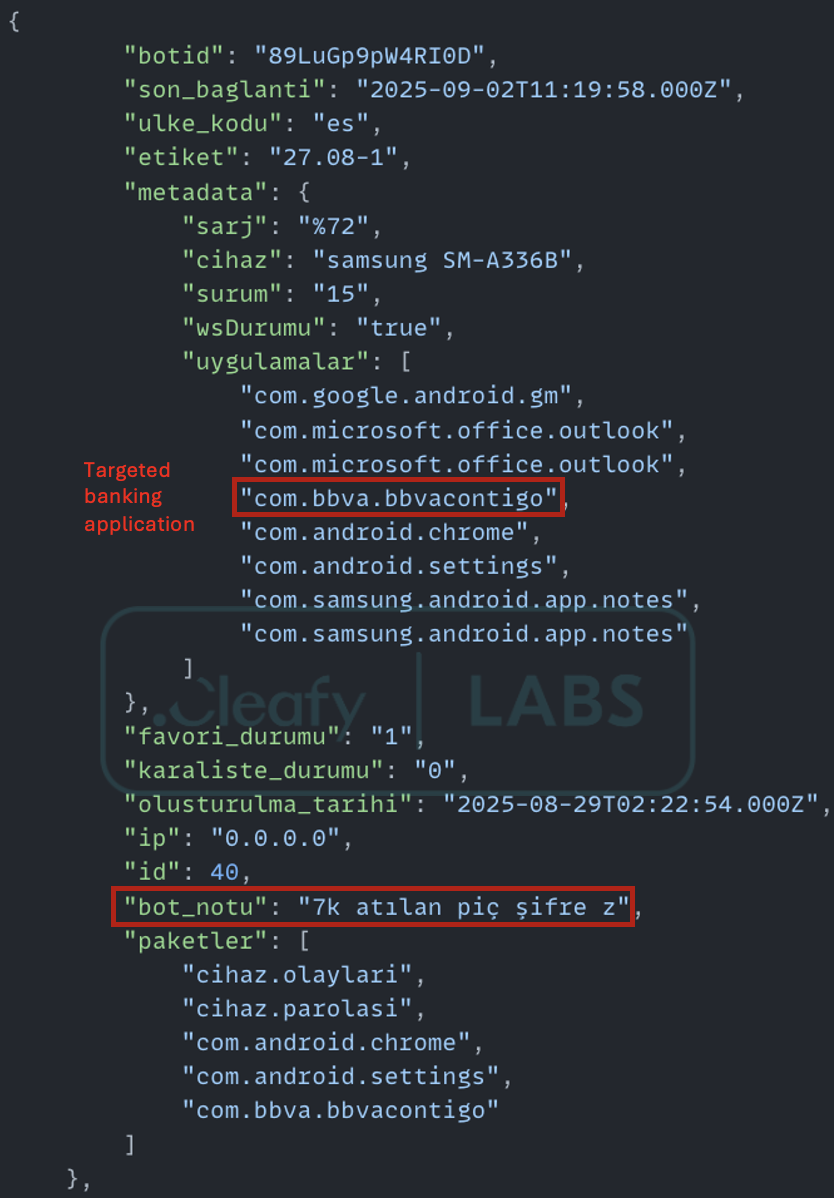
This short phrase, written in colloquial and vulgar Turkish, is extremely significant. An analysis of the note suggests the following:
This note alone provides overwhelming evidence. It confirms the language and shows a human operator actively engaged in fraud attempts, documenting victim device details (like the unlock pattern) for future access. Further examples reinforced this TTP, with notes like "desen M" ("desen" is Turkish for "pattern") and numeric PINs like "4758" and "12369" found in other bot records.

The linguistic consistency between the malware's code, the C2 panel interface, and the colloquial operational notes from the operators themselves strongly suggests a vertically integrated criminal operation. This is not a Malware-as-a-Service model, where developers of one nationality sell their tools to customers of another. Instead, it indicates a cohesive Turkish-speaking group managing the entire attack lifecycle, from code development to victim monetization.
The investigation into the Command and Control (C2) infrastructure between August and September 2025 provided direct visibility into Klopatra's active campaigns. Although this visibility may be partial, the data collected from the three main servers offers valuable insights into the group's operations and TTPs.
The analysis revealed two main campaigns managed by dedicated C2 servers with a clear geographical focus.
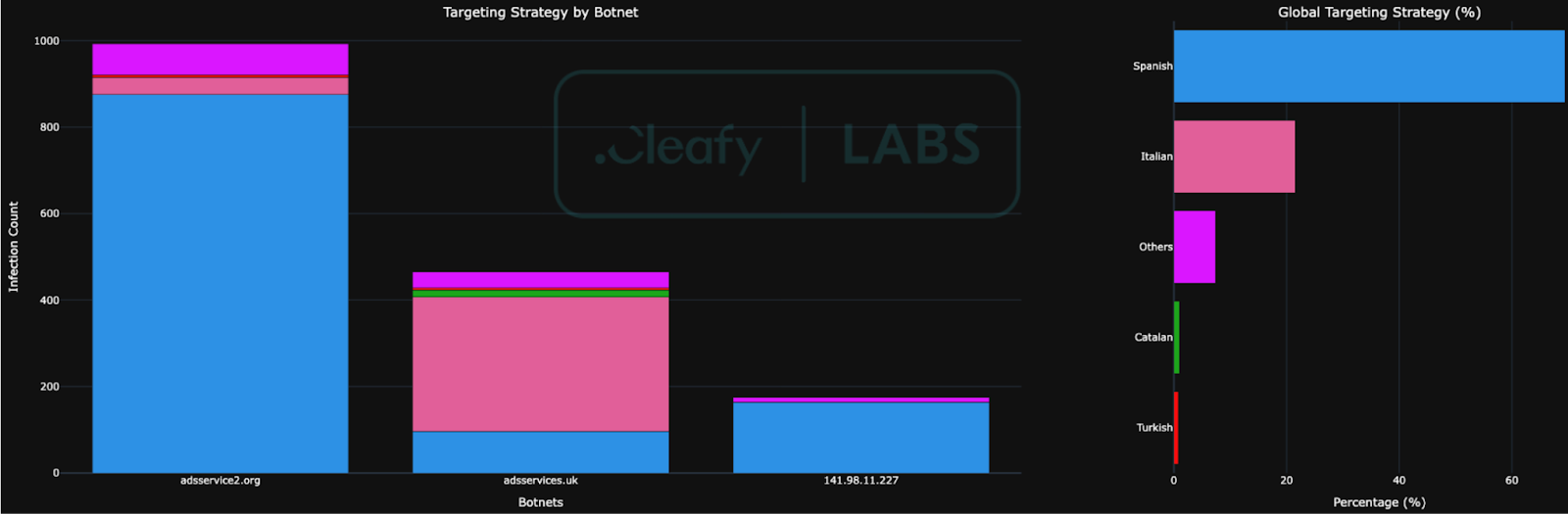

The third identified server, guncel-tv-player-lnat[.]com, had a very different profile. It hosted only 9 bots scattered across various locations (Georgia, Kuwait, Qatar) and with an inconsistent set of targets. All evidence suggests that this server is not part of a large-scale campaign but rather serves as a staging or testing environment for the malware developers. This provides insight into the actor's development lifecycle, showing where they might test new features before deploying them to the main botnets.
As is common practice for TAs, Klopatra's operators used Cloudflare to mask the true IP addresses of their C2 servers. Whois records confirmed that Cloudflare was used as both the registrar and the nameserver, making direct identification via standard DNS lookups difficult.
Despite this layer of obfuscation, it was possible to identify the origin IP addresses. This de-anonymization was likely the result of an operational security (OPSEC) mistake by the actors. By leveraging network asset intelligence platforms, it was possible to uncover misconfigurations. The most likely scenario is that the operators pointed the domains directly to their server IPs during the initial setup phase, before correctly configuring the Cloudflare proxy. This error permanently exposed the true server location to historical analysis tools.
This discovery allowed for the localization of the main infrastructure and the linking of the two main campaigns :
The definitive proof of this link was obtained by accessing the C2 endpoint through the Cloudflare-protected domain and directly via the discovered origin IP, obtaining identical responses in both cases.
*The “Bot Count” metrics were derived from a specific C2 endpoint that lists all connected bots. This data includes a progressive'id'field, which increments with each new infection. The numbers presented in the table reflect the highest 'id' value observed for each server during our last data extraction on September 22, 2025.
Klopatra is not a static threat. The analysis shows it is under an active and rapid development cycle, with the authors constantly refining its capabilities and evasion techniques.
Targeted threat hunting operations, using unique artifacts from the initial sample as pivot points (package name, signing certificate), identified nearly 40 related samples. Among these, one discovery proved crucial: a development or test build of Klopatra that was not protected by Virbox. This unobfuscated sample acted as a "Rosetta Stone," allowing for a complete reverse-engineering of the malware's core logic, understanding its C2 mechanisms, and discovering the full range of its capabilities.
This collection of samples has made it possible to outline at least three distinct evolutionary phases:
Moreover, recent builds include more commands related to the UI Overlays and Injections and advanced permission management, which are crucial for effective banking trojans.
This progression from a basic version to a feature-rich and heavily obfuscated one highlights the malware authors' rapid iteration and adaptation. This agile development cycle indicates a dedicated and responsive adversary.
Klopatra's technical capabilities are not just theoretical. Through incident response activities and the real-time visibility provided by the Cleafy platform, our team was able to reconstruct the precise TTPs used by the operators in a live fraud scenario. A clear picture of a sophisticated, hands-on keyboard attack emerged by correlating data from victims' devices, our platform's telemetry, and the malware's code.
The operators show a clear preference for conducting their attacks during the night. This timing is strategic: the victim is likely asleep, and their device is often left charging, ensuring it remains powered on and connected. This provides the perfect window for the attacker to operate undetected.
The attack unfolds in a carefully orchestrated sequence:
The following screenshot from the Cleafy console shows the detection of the first nocturnal fraud attempt (patient zero). The platform identified a high-risk session from a compromised device in the middle of the night.

A detailed view of the session reveals the operator's actions: a rapid succession of instant payment attempts to a new bank account.

This use case demonstrates the seamless integration of Klopatra's automated capabilities with direct, manual intervention by a human operator. It transforms the malware from a simple data-stealer into a direct, real-time financial theft tool, highlighting the critical need for combining malware detection, behavioral capabilities, and transactional data to detect such sophisticated attacks.
Klopatra represents a significant and sophisticated threat to the financial sector and mobile device users, particularly in Europe. The analysis conducted by the Cleafy team revealed malware that is not only technically advanced but is also managed by a cohesive and disciplined Turkish-speaking criminal group, controlling operations from A to Z.
Its main innovation—adopting commercial-grade protections like Virbox, combined with an architecture based on native code—marks a turning point in the Android malware landscape. This approach, once the domain of desktop malware, is now a reality in the mobile world and serves as a harbinger of future trends. It is likely that other criminal groups will follow suit, making detection and analysis increasingly complex and resource-intensive.
The active campaigns in Italy and Spain, with over 1,000 confirmed victims, demonstrate that Klopatra is not an experiment but a fully operational and successful fraud tool. The agility shown by its rapid development cycle suggests that the operators will continue to refine their TTPs, expand their target list, and integrate new evasion techniques to stay one step ahead of the security community.
For financial institutions and anti-fraud teams, the emergence of Klopatra underscores the need for threat detection solutions that go beyond static analysis and focus on device-level behavioral monitoring. For the threat intelligence community, continuous monitoring of this group and its infrastructure will be essential to anticipate their next moves and protect users from this evolving threat.
Klopatra samples:
C2 Infrastructure:
Be among the first people worldwide to receive comprehensive technical reports on newly uncovered threats.
Subscribe now